In-Depth
Ramsomware Poses New Threat to Users
A new exploit poses as law enforcement to trap users into paying to unlock their system What you need to know about the exploit and how to keep your users safe.
By Alvin Estevez
In the last two months, there has been a dramatic spike in a relatively new kind of malware. It’s called ransomware and it’s the next evolution in the efforts of Internet thieves to separate unsuspecting victims from their money. This time, they’re pretending to be law enforcement agencies collecting fines for illegal computer activity. Perhaps even more disturbing is the way these crooks are collecting their “fines.”
Here’s how the police ransomware scam works: Internet crooks create a malware infection that gets onto a computer any number of ways: phishing e-mails, ads on adult Web sites, downloadable executable files posing as video player codecs, etc.
Some time later, the victim’s screen freezes and a message pops up with an official looking law enforcement logo telling them their computer has been frozen because of suspected illegal activity. Note the FBI header (see figure below) from an infection called FBI Moneypak.
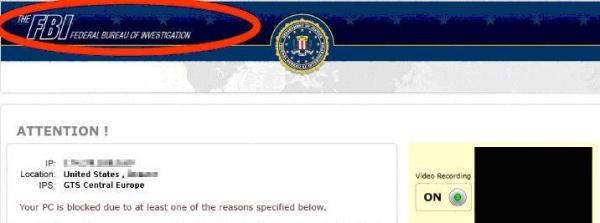
This particular message tells the victim someone using their computer is suspected of everything from “illegally using or distributing copyrighted content” to viewing and distributing child pornography. The only way to “unlock” your computer is to pay a “fine. Note the “Video Recording” icon in the lower right hand part of the screen. This infection even turns on your computer’s web camera to make it seems as though your image is being recorded and sent to authorities.
Although these police ransomware infections have been around for a while, in the last few months, they have spiked dramatically. At SpyWareRemove.com, a site that tracks malware infections, we’ve seen a jump in traffic of 460 percent for the FBI Moneypak infection in early October alone.
The UKash virus is a similar ransomware infection, this one purports to be from a European law enforcement agency.
UKash and the FBI Moneypak infection currently account for more than 25 percent of the people coming to SpyWareRemove.com looking for help to remove infections.
These ransomware infections are particularly effective because many times they are planted in somewhat seedy corners of the Internet: porn sites and movie download sites. The victims may have actually been doing some of the activities these fake police messages allege, which may make folks think the warning is legit.
How do these fake infections collect their “fines”? That’s a new wrinkle as well. Most scareware or ransomware requires you to actually make a credit card payment of some sort. The hackers can only collect money if they can find a way to process those payments. Many times they will find a shady processor overseas in Russia or Eastern Europe.
International authorities are cracking down on these kinds of payment processing centers. Although this makes it harder for cybercriminals to collect money, they’ve figured out a way around the credit card processing problem. Instead of asking for your personal credit card number, these infections instruct their victims to use a pre-paid debit card -- the kind you can buy at a grocery or convenience store. Instead of actually processing a payment, the criminals sell the pre-paid debit card numbers on the black market. We suspect that a growing number of malware makers will start using this tactic.
Staying Safe
It’s hard to pinpoint exactly what kind of Web sites or locations are the most common source of police ransomware infections. The cybercriminals tend to move these infections around. Sometimes they come in the form of infected ads on Web sites that users may visit. Sometimes they come in the form of sketchy video codecs or executable files that users try to install. Other times they come in the form of e-mail spam. Many of the users we have helped at SpyWareRemove.com say they have no idea how the ransomware infections got on their computers.
The first clue people may have that their computer has been compromised is when that law enforcement warning screen pops up. There is no legitimate law enforcement agency that would lock your computer for suspected crimes and require an immediate payment to unlock it, and most users realize this. However, there are enough people who get scared and actually enter payment information to make this scam worthwhile.
One other clue that this isn’t a genuine law enforcement action is the wording of the warning itself. Many of these infections are created by Eastern European and Russian cybercriminals for whom English isn’t their native language. They try to make the police warning sound legitimate, but some of the phrasing is awkward -- a sure giveaway.
For example, the FBI Moneypak infection warning letter has awkward phrases such as, “You have been violation Copyright and Related Rights law” and “a fine of two to five hundred minimal wages.”
The best way to protect users from getting these infections in the first place is by having a trusted and fully updated anti-virus and anti-malware program installed on their computers. The vast majority of the infections we track are hitting computers that either have no anti-virus/anti-malware protection or have protection that has not been updated.
Even with that kind of protection, users should be wary of strange e-mail attachments or prompts to download video codecs or executable files from questionable Web sites. A little bit of protection and a lot of common sense can help keep the police ransomware infections off your computer and out of your wallet.
Alvin Estevez is the CEO of Enigma Software Group and editor of www.SpywareRemove.com, a site devoted to malware information. You can contact the author at editor@spywareremove.com.