
BlueData Software launched its EPIC Enterprise platform with the goal to "democratize" Big Data by making it more accessible to enterprises of all sizes

Red Hat announced it's now seeking to become the king of the enterprise cloud services vendors.

Business continuity services mitigate disruption risks and provide for disaster recovery.
Business stakeholders, designers and developers can keep track of an app's UX throughout a project lifecycle.

Move will will add enterprise mobility capabilities to Red Hat's JBoss Middleware and OpenShift Platform-as-a-Service (PaaS) offerings.

Developers and rogue enterprise users can cause problems.
China heads outside threats that could shake up everything far more than upstart technologies like software-defined networking.

Recently a group of so-called "pacesetter" companies surveyed by IBM's Center for Applied Insights reported forming new partnerships with "citizen developers" to bridge skills gaps in their workforce, adding to the mounting evidence of crowdsourcing's traction in the enterprise.

Real Status Ltd. today announced the general availability of Hyperglance version 3.3 to manage enterprise cloud and SDN systems.

Pivotal Software is capitalizing on last year's acquisition of mobile development firm Xtreme Labs with the recent announcement of Pivotal CF Mobile Services.

Latest forecast sees 89 percent compound growth leading to $8 billion market by 2018.
Gartner and IDC analysts provide tips on how to succeed in the new mobile world.
GigaSpaces Technologies and RackWare each release 3.0 versions of their software for enterprises doing business in the cloud.

Traditional ERP and CRM enterprise software vendor joins archrival Oracle as sponsor of OpenStack Infrastructure-as-a-Service initiative.

Acquisition of BlueKai Audience Data Marketplace pays off with product designed to help enterprises target customers.

Technical and financing agreements are latest in competition among Hortonworks, Cloudera and MapR.

Big Switch Networks Inc. flagship product provides hyperscale networking technologies.

Companies emphasize bringing Big Data analytics to iPhone and iPad users.

Vendors scramble to help enterprises move their Big Data analytics to the cloud in an exploding market.
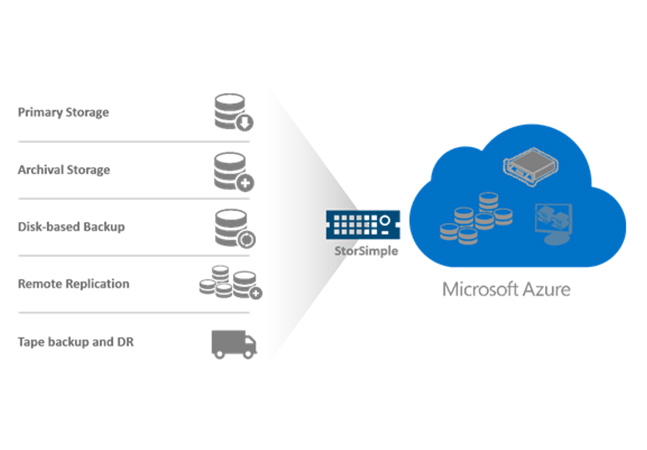
Microsoft announced this week a new line of its StorSimple appliances that link on-premises datacenters to the Azure cloud.