In-Depth
Three Trends Driving Data Security Strategies in 2012
In 2012, businesses must align data security with customer value.
By Ulf Mattsson, Chief Technology Officer of Protegrity
With all the high profile breaches of customer data we've seen this year (Sony, Citi Corp, Epsilon, and more), consumer confidence in current data protection standards is on shaky ground. Class-action lawsuits are flying, businesses are paying millions in compensation, and it's clearly time for a major attitude adjustment towards data protection. In 2012, businesses will focus on determining how much they are willing to invest to protect their customers' personally identifiable information -- through secure storage, compliance with legislation, and the tools required to accomplish those tasks effectively.
The following three trends will drive 2012 data security strategies.
2012 Prediction #1: Cloud computing will hit a wall
Security is proving to be the 800-pound gorilla at the cloud computing party. Businesses have no control over the security of their sensitive data in the cloud -- they may not even be able to control their own PCI-DSS certification audits. They're responsible for the data but have no direct control over the mechanisms to protect it.
The advantages of cloud solutions are myriad -- reduced infrastructure costs, ease of growth, providing a consistent experience for local and remote users. Compliance in the cloud can be expensive -- tier-1 merchants are spending an average of $225,000 a year on keeping compliant, as well as committing resources for months at a time. Virtual data centers, while delivering many of the same benefits, take the problem a stage further by adding multitenancy to the mix. PCI regulations don't yet cover the maintenance of secure data storage protected by Chinese walls, but it's going to come. Resource sharing is never good for security and compliance -- it only increases the attack surface.
Then there's SaaS. Only paying for what you use sounds great, but you're also storing all that valuable customer data out on the Internet in a virtual data center. Same audit problems, same security responsibilities. Just ask Citibank how well SaaS worked for them when their customers' personal information was exposed through security failures at Epsilon, the world's largest e-mail marketer.
In 2012, we will see PCI audits become more expensive thanks to the cloud because when a cloud-based environment is involved, auditors must make their assessments on the basis of all requirements in both the merchant's and the cloud vendor's environments -- and remember, merchants have no direct control over third-party security measures.
We're also going to see additional mandatory requirement for safeguarding PII because companies have simply not been doing enough on a voluntary basis. Senator Richard Blumenthal (D-CT) has introduced the Personal Data Protection and Breach Accountability Act of 2011 to protect individuals' personally identifiable information from data theft and penalize firms that don't adequately secure customer information.
Businesses will no longer be able to avoid addressing cost-effective security and management in the cloud if they want to continue to reap the benefits of cloud computing. Without alternative data protection strategies that will allow them to realize the business benefits of the cloud while retaining their compliance certification and reining in runaway compliance costs, further growth of the cloud sector will not be possible.
2012 Prediction #2: Monitoring will go into terminal decline
Passive monitoring tools such as Security Information and Event Management (SIEM) for unauthorized or otherwise inappropriate activity is completely ineffective in the face of the tens of thousands of assaults on corporate networks every day. Today's attacks are sophisticated and stealthy -- they'll be in and out (with your data) before the log even reaches your desk. Actions are rendered even easier by the widespread disabling of monitoring systems after the auditor has left the building.
Monitoring is extremely valuable in today's Big Data world, answering questions such as: Who's using which apps for what purpose? Which Web pages are holding visitors' attention the longest? How many shoppers abandon their carts, and at which point in the transaction process? However, catching bad guys is not one of its key strengths. It's a lagging indicator, not an early warning system. By the time you spot a trend, you've probably already lost control of your network to the attacker. According to Verizon's 2011 Data Breach Investigations Report, conducted in cooperation with the U.S. Secret Service and the Dutch High Tech Crime Unit, the single least-effective data protection method used today is monitoring.
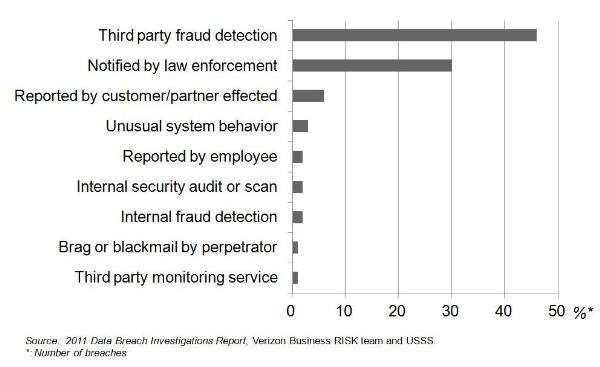
Fig 1. Breach discovery methods
Instead, companies in 2012 will be looking for proactive high-performance, cost-effective ways to address the ever-growing issue of end-to-end protection of PCI, PII, and PHI data.
According to Adrian Lane at security research firm Securosis, "given the rapid evolution of SIEM/Log Management offerings -- and the evolution of requirements with new application models and this cloud thing -- [businesses] should be wondering whether there is a better, easier, and less expensive solution to meet their needs."
2012 Prediction #3: Companies must align their security investments with customer value
During one of this year's multiple breaches at Sony, unencrypted data (including passwords and personal details) were stolen and the hackers made off with millions of names, addresses, passwords, e-mail addresses, birth dates, phone numbers, and payment cards. Sony's stock value dropped 30 percent after attacks were disclosed; there's no way to quantify how many customers decided Sony didn't place enough value on their customer relationship to protect it from what were in essence fairly unsophisticated SQL injection attacks.
Financial services companies have been hit hard and frequently enough by hackers to spend some serious financial and public relations capital on customer data privacy protection. Hackers are moving to easier targets, and it's likely we'll see significant increases in attacks on less well-protected sectors such as hotels, retail environments, and health care, where sensitive data is shared across multiple channels and points of contact. End-to-end data protection will become a prerequisite for good customer relationships and consumer confidence.
An additional complicating factor for these businesses is the rapid growth in the use of mobile devices to process transactions, rendering that data even more vulnerable and further increasing the need for seamless protection of data, no matter whether it is in transit or at rest. Businesses and vendors alike must address the entire customer data life cycle, regardless of the points in that life cycle at which the customer actively engages with the transaction processing system.
This year's Verizon Data Breach survey found that almost 90 percent of all businesses were out of compliance with PCI-DSS requirements at the time of their most recent breach. Not surprising, since the Cisco PCI-DSS 2011 survey noted that more than 60 percent of all merchants in the United States spent between $100,000 and $1,000,000 on compliance. Even Level 3 merchants -- those processing between 20,000 and 1,000,000 transactions per year -- were spending an average of $155,000 per year excluding assessment costs according to Gartner.
Companies are putting significant resources, both financial and human, behind data protection but still flunking compliance certification. Clearly there's a disconnect which I believe can be resolved quite easily by focusing on the value of the customer relationship connected to the data, not the nature of the threat. Look for new solution packaging and pricing models to come into play that reflect this attitude adjustment, because continuing budgetary pressure will drive new thinking. This will, in turn, force businesses to put a price on that most valuable and least tangible asset -- their reputation.
Ulf Mattsson is the chief technology officer of Protegrity, an enterprise data security management solutions provider, where he created the architecture of the Protegrity Data Security Platform. He is considered one of the founding fathers of tokenization and has been advising the industry's top analysts and stakeholders including PCI Security Standards Council, ISACA, and Visa as they navigate the role of tokenization in payments security. Prior to joining Protegrity, Mattsson spent 20 years with IBM working in software development as a consulting resource to IBM's research organization, specializing in the areas of IT architecture and IT security. You can contact the author at [email protected].