In-Depth
An Introduction to Deep Content Inspection
Traditional deep packet inspection may no longer be able to protect your environment. We look at a new approach -- deep content inspection.
By Dr. Hongwen Zhang
As network traffic increases in volume and complexity, malicious content and attacks are evolving. Traditional network filtering technologies are limited in their ability to protect against these new threats. In 2011, Microsoft reported that one in every 14 downloads contained malicious content. Weak or inadequate filtering technologies allow malicious content to pass onto the network undetected. Consequently, organizations will suffer reputational, operational, and customer relationship management challenges, as well as information leakage and IT infrastructure damage.
The PwC 2012 Global State of Information Security Survey shows that a mere 43 percent of security experts are confident in their information security strategy. An array of security threats has transpired with the proliferation of mobile data usage, social media, HTML5 and cloud computing. Standard inspection technologies that secure networks at the packet level, such as deep packet inspection (DPI) and packet filtering, are inefficient and unable to scale to provide safe use of the new Internet.
Deep Packet Inspection Limitations
Today, DPI is the most widely adopted technology for monitoring and managing network packet data. It secures networks by matching the IP packet sequences against a known set of offending patterns. However, to be effective, DPI must match the packet information to these patterns in real-time wire speed, which presents two limitations.
First, at any given time, a DPI chip is capable of holding only a limited number of packets for pattern matching. To transmit an application payload, the number of IP packets needed often exceeds the number of packets a DPI system can inspect. As a result, malware embedded in large application payloads will pass through.
The second problem presented by DPI is the limited amount of memory available for pattern matching. The packet data obtained from a DPI system must be matched against a known malware threat. However, the number of unique signatures the system uses for matching is restricted.
An inept DPI system is not able to properly secure a network. As a result, unsupported application types as well as nested, ZIPped, or archived files will easily slip through a DPI security solution and onto the network undetected.
Benefits of Deep Content Inspection (DCI)
To address undetected and emerging security threats, a new approach to data inspection that incorporates thorough analysis must be deployed on the network. DCI is an advanced form of network filtering that reassembles, decompresses, and/or decodes network traffic packets into their constituting application-level objects (often referred to as MIME objects). It functions as a fully transparent device at a more comprehensive level than DPI; as such, it does more than simply check the body or header of data packets moving through a network. Instead, a DCI solution examines the entire object so that any malicious or non-compliant intent is detected.
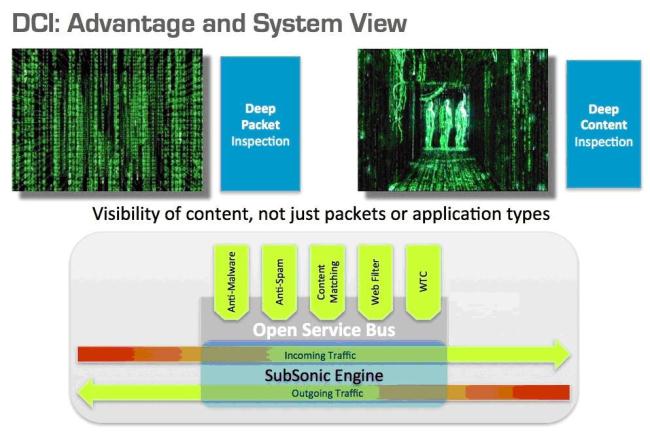
To understand the intent of data-in-motion, modern DCI technology performs full content-based inspection in real time. As a result, DCI gains a broader inspection scope than would be available by exclusively matching packet sequences against patterns. In addition, DCI is able to perform a reputation search and behavior analysis on structured or packed data, resulting in a new level of protection. By monitoring content across multiple packets, DCI is able to discover and evaluate signatures that cross packet boundaries.
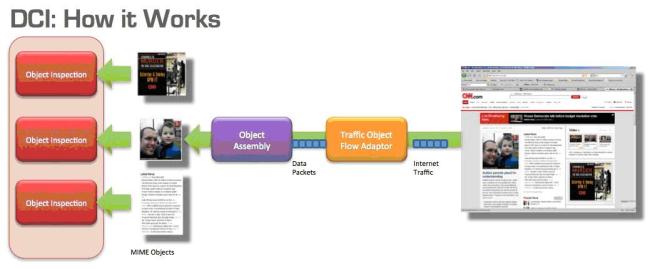
By moving away from traditional packet inspection and concentrating on the content and intent of data, DCI is better equipped to screen for attacks and malicious content and effectively secure enterprises, government organizations and service providers against today's new and evolving threats.
Dr. Hongwen Zhang is president and CEO of Wedge Networks, a provider of remediation-based deep content inspection for high-performance, network-based Web security. He holds a Ph.D. in Computer Science from the University of Calgary; a MSc in Computer Engineering from the Institute of Computer Technology - Chinese Academy of Sciences (Beijing, PRC), and a Bachelor of Science in Computer Science from Fudan University (Shanghai, PRC). With more than two decades of high-tech leadership experience, Dr. Zhang is a co-inventor and holder of several patents in the area of computing and networking. You can contact the author at [email protected].