In-Depth
How to Avoid NAC Pitfalls with a Standards-Based Approach
With so many benefits to reap from network access control, why aren't all IT shops on board?
by Lisa Lorenzin
Network Access Control (NAC) can be a powerful weapon in the enterprise security arsenal. Correctly deployed, NAC offers benefits ranging from network protection and restriction of application access to regulatory compliance enforcement and auditing. In addition to its general benefits, NAC can address specific problems such as secure provisioning of access to guest users, differentiation of corporate assets from non-corporate equipment, and automatic remediation of non-compliant devices.
Business drivers for NAC include protecting corporate resources from unauthorized users, limiting the impact of security breaches, network segmentation, increasing the overall security posture of the network, and meeting regulatory requirements, among others. Enterprise security policy can be applied across multiple data centers, dozens of servers, hundreds of remote offices, and/or thousands of end users, reflecting numerous levels of privilege and a range of resources with diverse trust requirements.
Given the obvious benefits of NAC, why isn't everyone doing it?
The Challenges of NAC
Today, NAC suffers primarily from a public relations problem: enterprises often perceive it as difficult, or even infeasible, to implement in their environment due to the challenges involved. These obstacles include:
Vendor lock-in: Proprietary solutions work only with a single vendor's products for policy management, enforcement, and/or endpoint software. This puts the enterprise at the mercy of a single technology provider, and in extreme cases, a proprietary NAC implementation can require bulk replacement of network components.
Daunting effort: Most enterprise networks are complex enough as they stand! Adding more moving parts that have to interface with the whole just compounds the problem. Additionally, an enterprise may want to apply network access control to a wide range of locations and a variety of user communities, in which case deployment planning can rapidly become overwhelming.
Indirect costs: Adding new security controls often leads to conflict with existing business procedures. The results can include confusion, frustration, and -- at worst -- potential downtime, which directly affects the productivity of the work force and possibly the profitability of the company. Additionally, users faced with new processes or newly-restricted resources will often pick up the phone, driving up help-desk call volume.
Uncertain future: Many competing approaches to NAC exist today -- endpoint-based vs. network-based, inline vs. out-of-band, point products vs. large NAC frameworks. How do you find a solution that will scale to meet your network's needs today and for years to come?
Given that list of caveats, the question becomes: how can anyone deploy NAC while minimizing potential negative consequences? One way to address -- or, better yet, avoid -- many of these issues is to pursue a standards-based approach to NAC.
Trusted Network Connect: Standards-Based NAC
The Trusted Computing Group (TCG) is a not-for-profit organization formed to develop, define, and promote open, vendor-neutral industry standards for trusted computing across multiple platforms. TCG has developed open standards for NAC, freely available for anyone to implement, called Trusted Network Connect (TNC). TNC is completely vendor-neutral, offering strong security and broad interoperability; TNC-based products have been available for more than four years.
TNC defines an architecture and the interfaces that allow interrogation of an endpoint to determine its integrity and compliance with security policies. The architecture starts with three primary components: an endpoint device requesting access to the network; an enforcement point (such as a firewall, VPN gateway, or 802.1X-enabled switch or access point) controlling access to the network by consuming and enforcing policy decisions; and a policy server that makes policy decisions and provisions them to the enforcement point.
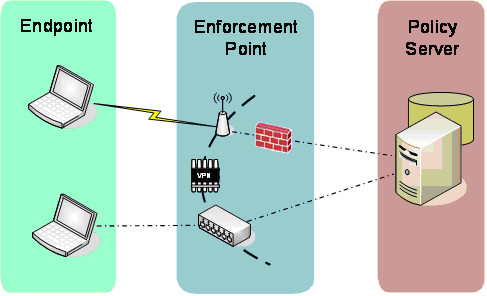
Figure 1: Basic NAC Architecture
TNC interfaces standardize communication between these components, enabling a policy server to interrogate an endpoint, determine user identity and endpoint integrity, and make an access control decision based on the resulting information. The policy server sends the policy decision to the enforcement point, telling it whether to permit, deny, or restrict the endpoint's access to the network.
Expanding the Playing Field
The TNC specifications include an interface, IF-MAP, which extends the TNC architecture to allow data sharing across a huge variety of security and networking systems. A metadata access point (MAP) provides a central clearinghouse for endpoint information, also called metadata. Other devices can publish, search for, and subscribe to notifications about that metadata. This extends the traditional NAC architecture to include additional network and security components such as intrusion prevention systems, vulnerability scanners, dynamic host configuration protocol (DHCP) servers, and even application servers. These components can act as sensors, adding data to the MAP, and/or act upon information received from other components.
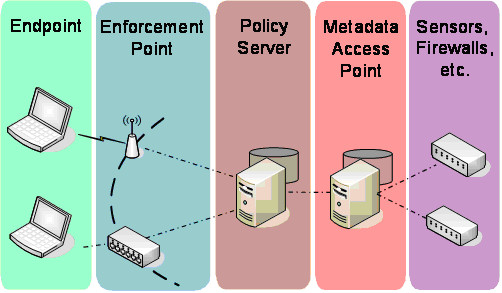
Figure 2: NAC Architecture with MAP Integration
In a common IF-MAP-enabled scenario, when a policy server authenticates an endpoint to the network, it publishes endpoint metadata (ranging from user identity and role to endpoint MAC address to network location) to the MAP and subscribes to information about that endpoint. A DHCP server then publishes metadata, mapping the endpoint MAC address to an IP address; an intrusion prevention system detects unauthorized activity by that IP address and publishes metadata on the violation.
The MAP notifies the policy server of changes to the metadata for that endpoint; because the endpoint has sent unauthorized traffic, the policy server dynamically alters its policy to limit the endpoint's access privileges, and the enforcement point implements the access restrictions. Each device may come from a different vendor; TNC implementation enables communication between components for dynamic, responsive protection.
Meeting the Challenges of NAC
NAC solutions built on TNC standards offer a wide range of advantages:
Avoid vendor lock-in with interoperability: Standards-based NAC implementations allow seamless creation of an access control overlay that works with existing network and security technology and allows integration of a variety of components from multiple vendors.
Flexibility minimizes deployment pain: Elimination of vendor lock-in enables the use of best-of-breed solutions in all aspects of the network. An open solution that integrates with existing equipment allows you to break a large or complicated NAC deployment project into smaller, simpler phases, reducing complexity. Tackle the low-hanging fruit first, then use the lessons learned to bootstrap subsequent, more challenging phases!
Reduce costs through reliability and end-user focus: Proven technology minimizes disruption of business practices and impact to productivity. Insulate users from disturbance by employing TNC-enabled features such as transparent application of restrictions, auto-remediation (automatic repair of non-compliant endpoints), and clear messages when user action is required. The result: lower support costs and higher user acceptance.
Plan for the future with evolving standards: The Internet Engineering Task Force (IETF) is now working on draft standards for NAC, using two TNC protocols as their starting point. TNC standards will maintain compatibility with the IETF's specifications, and TNC will continue to develop additional open standards to meet future as well as present needs.
Summary
TNC-based technology delivers vendor-agnostic support for diverse, heterogeneous networking environments, providing cost and deployment time reductions by leveraging installed products. Additional benefits of TNC include an alternative to single-vendor lock-in; thorough and open technical review of standards; and "future-proof" interoperability with imminent IETF protocols. A standards-based approach to NAC uses TNC-enabled solutions to build a solution that will grow with your network, ensure higher, faster ROI, and minimize the pain of NAC deployment.
Lisa Lorenzin is a principal solutions architect for security
solutions at Juniper Networks. You can contact the author at [email protected].